We’ve all been there – a client forwards individual emails to a someone in your firm. Those emails are then forwarded to your Litigation Support department for processing. You can either have the client start collection over, or redact the top half of each message. Or even better, the client tries to help by having their assistant print each and every responsive email, then scan them to PDF as a bundle.
There is a better way.
Getting electronic data delivered to your office in a manner that is reasonable and cost effective for the client, while providing you with usable data, can be a relatively simple process. In Litigation Support, you play an important role in assisting the client navigate the complex and often confusing world of eDiscovery.
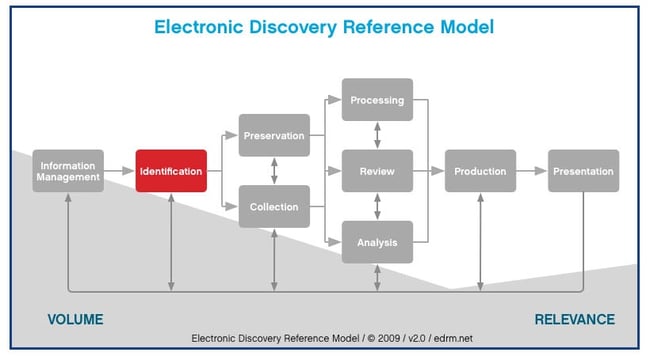
Before you can preserve and collect data, it must be identified. Identification is the process of figuring out who has data and where it’s located. The earlier this step begins, the easier it will be to collect data in a convenient way. In my experience, it’s best to begin considering document collection as soon as you find out the client is contemplating litigation. Establishing your department as an early contact point will enable you to provide input throughout the process and to manage expectations and costs over the lifecycle of the project.
Step 1: Identify WHAT
What types of files and material are relevant to the issues in question? Email usually plays a huge role, but it’s also important to consider less common sources such as reports generated from proprietary software, client account summaries, PDFs, voicemails, text messages, videos, contracts, off site paper records, log books, and engineering drawings or maps (to name a few). Discuss with the client the different types of records that were created both manually and automatically. A clear understanding of the issues will help you ask the right leading questions to make sure all sources are considered. A highlighter and copies of the pleadings will go a long way to providing you with the information you require for this step.
Step 2: Identify WHO
Custodians are the people who possess data related to the file; these people need to be identified as soon as possible so their data can be preserved (that comes later). Work with the client to establish a list of all custodians who may be in possession of data identified above. A first draft of the list may contain anyone who was involved in any way, whereas future versions may be narrowed down to key custodians. The scope of the custodian list depends on a number of factors specific to the file, and should be discussed with the legal team and client to make the best decision.
Step 3: Identify WHERE
Data can be located on computer hard drives, backup systems, network shares, remote servers, cloud storage, media devices, off site records facilities, cell phones or any other number of sources. Because of the vast number of possible data locations, it is important to spend ample time evaluating where relevant data might exist. Clients may have policies for data storage, but that doesn’t mean custodians follow all the recommendations. A number of methods can be used to identify the various data storage locations; the most common being the custodian interview.
Remember that data may exist that doesn’t belong to a specific custodian. Accounting data is a common example. After interviewing all custodians, discuss this with the client to determine if any shared locations contain data that was not identified through the individual custodian collections.
Step 4: Identify HOW
Knowing what you’re looking for, who has it, and the likely locations of data storage is only half the battle. The final step in Identification is to plan HOW you will retrieve the records. There are many methods to consider, including search terms, manual collection, date ranges, and data type restrictions. Remember that there are flaws with each type of collection. For example, not all documents are searchable, and therefore would not be caught by search terms. Identify and weigh the risks, and determine the best possible method. Documenting your decisions (and reasoning) is an important step in creating a defensible process.
Simplified Identification Table
Following is a simplified identification table that can be used to record the 4 components of identification discussed above. Click on the image to download an editable version in Excel format. It should be modified and expanded as required to meet the needs of your file(s).
The EDRM also provides a thorough guide for the identification process, which can be viewed here: www.edrm.net/resources/guides/edrm-framework-guides/identification
Litigation can vary tremendously in scope, resulting in vastly different Identification, Preservation and Collection processes. Considerations around the type of client, number and location of offices, and manner in which they organize and backup their data will also impact decisions that need to be made. Generalizations apply however, and they can help you establish your own internal policies and procedures.
Don't miss the opportunity to learn firsthand how the EDRM applies to your firm. Come see Tiana Van Dyk at Technology in Practice 2015 in November at the Four Seasons Hotel, Toronto. Register today!